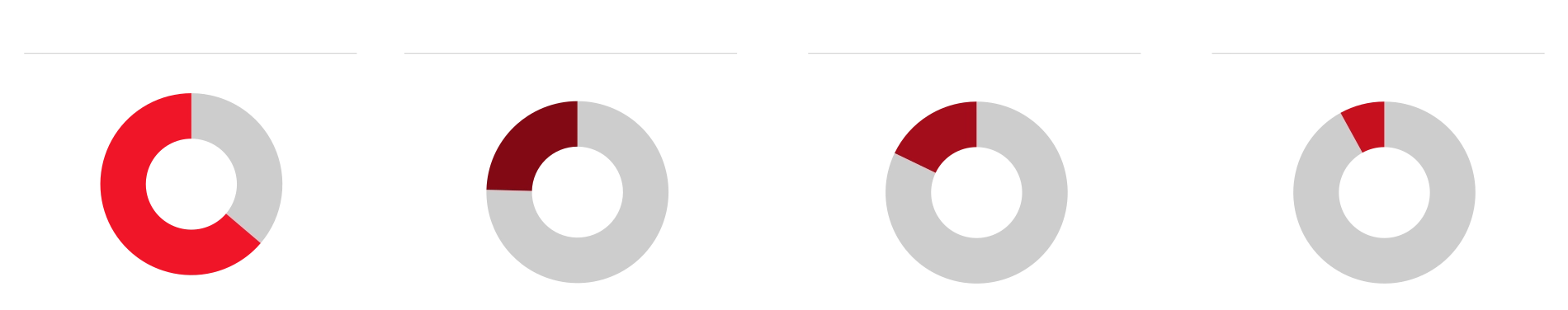
Phishing: Testing inbox resilience
Phishing is still the most widespread attack. As part of our service we prepare a tailored phishing campaign that simulates real threats - from generic messages to sophisticated spear phishing targeting specific departments or individuals. We measure how many employees click the link, enter credentials, or download a file.